CyLR — Live Response Collection tool by Alan Orlikoski and Jason Yegge
(1)
Download CyLR for Windows
https://github.com/orlikoski/CyLR/releases
(2)
Run CyLR.exe
(3)
Export Collected Files
(4)
Get-FileHash (for Forensically Sound)
(5)
Check out collected files
(6)
Check out event logs
(7)
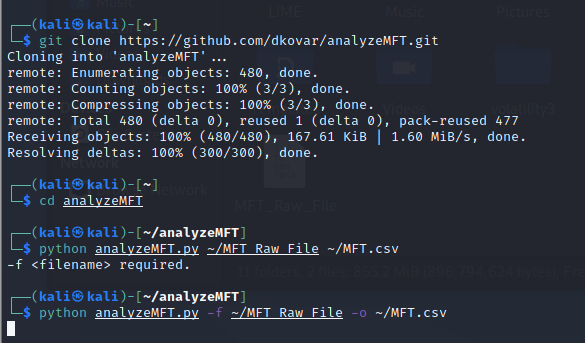
How to convert MFT to CSV?
Move the MFT file to a VM with Pyhton2
Install pip
Download analyzeMFT - https://github.com/dkovar/analyzeMFT
It requires Python2 - it does not work with Python3
Move MFT.csv file to Windows again
(8)
Analyze MFT File
(9)
Analyze more
What does CyLR collect from a Windows OS:
- %SYSTEMROOT%\Tasks\**
- %SYSTEMROOT%\Prefetch\**
- %SYSTEMROOT%\System32\sru\**
- %SYSTEMROOT%\System32\winevt\Logs\**
- %SYSTEMROOT%\System32\Tasks\**
- %SYSTEMROOT%\System32\Logfiles\W3SVC1\**
- %SYSTEMROOT%\Appcompat\Programs\**
- %SYSTEMROOT%\SchedLgU.txt
- %SYSTEMROOT%\inf\setupapi.dev.log
- %SYSTEMROOT%\System32\drivers\etc\hosts
- %SYSTEMROOT%\System32\config\SAM
- %SYSTEMROOT%\System32\config\SOFTWARE
- %SYSTEMROOT%\System32\config\SECURITY
- %SYSTEMROOT%\System32\config\SOFTWARE
- %SYSTEMROOT%\System32\config\SAM.LOG1
- %SYSTEMROOT%\System32\config\SOFTWARE.LOG1
- %SYSTEMROOT%\System32\config\SECURITY.LOG1
- %SYSTEMROOT%\System32\config\SOFTWARE.LOG1
- %SYSTEMROOT%\System32\config\SAM.LOG2
- %SYSTEMROOT%\System32\config\SOFTWARE.LOG2
- %SYSTEMROOT%\System32\config\SECURITY.LOG2
- %SYSTEMROOT%\System32\config\SOFTWARE.LOG2
- Program Data (ie C:\ProgramData):
- %PROGRAMDATA%\Microsoft\Windows\Start Menu\Programs\Startup\**
- Drive Root (ie C:\)
- %SYSTEMDRIVE%\$Recycle.Bin\**\$I*
- %SYSTEMDRIVE%\$Recycle.Bin\$I*
- %SYSTEMDRIVE%\$LogFile
- %SYSTEMDRIVE%\$MFT
- User Profiles (ie C:\Users\*):
- C:\Users\*\NTUser.DAT
- C:\Users\*\NTUser.DAT.LOG1
- C:\Users\*\NTUser.DAT.LOG2
- C:\Users\*\AppData\Roaming\Microsoft\Windows\Recent\**
- C:\Users\*\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
- C:\Users\*\AppData\Roaming\Mozilla\Firefox\Profiles\**
- C:\Users\*\AppData\Local\Microsoft\Windows\WebCache\**
- C:\Users\*\AppData\Local\Microsoft\Windows\Explorer\**
- C:\Users\*\AppData\Local\Microsoft\Windows\UsrClass.dat
- C:\Users\*\AppData\Local\Microsoft\Windows\UsrClass.dat.LOG1
- C:\Users\*\AppData\Local\Microsoft\Windows\UsrClass.dat.LOG2
- C:\Users\*\AppData\Local\ConnectedDevicesPlatform\**
- C:\Users\*\AppData\Local\Google\Chrome\User Data\Default\History\**
- C:\Users\*\AppData\Local\Microsoft\Edge\User Data\Default\History\**
by dfirist@gmail.com












You can also use Eric Zimmerman's tool for parsing the MFT data.
ReplyDelete