(0) Methodology
--> Identify suspicious connection
--> Capture network traffic
--> Identify suspicious processes
--> Check user accounts and groups
--> Identify last log-ins log-outs
--> Check command-line, bash and logIns/logouts history
--> Monitor HTTP -HTTPS traffic
--> Monitor DNS Queries
--> Examine newly created files
--> Find persistent mechanism
--> Check activity and download history on browsers
sudo netstat -tnp > connections.txt
--> it will give connections and connection attempts.
(2)
sudo lsof -i -P > connections2.txt
--> it will give connections and connection attempts including domains.
(3)
sudo lsof -i -P -n > connections3.txt
--> it will give connections and connection attempts with IP addresses.
(4)
sudo tcpdump -i eth0 -w networkcapture.pcap
--> it will give a network packet flow sample. run this command 1 minute and cancel with CTRL+C
(5)
sudo ps -eo pid,%cpu,%mem,command --sort=-%mem > processes.txt
--> it will give running processes sorted by CPU usage including PIDs and full commands.
(6)
sudo cat /etc/passwd > users.txt
--> it will give the created user accounts to see if any malicious creation. (Hint: Malicious accounts can be found under bin/bash folder and )
(7)
sudo cat /etc/group > groups.txt
--> it will give information about who is sudo and admin to see if any malicious sudo account. (if it does not work try "sudo su" at first.)
(8)
sudo last -F > lastloginslogouts.txt
--> -it will give information about all users logged in and out (if it does not work try "sudo su" at first.)
(9)
sudo su
history > sudosuhistory.txt
--> -it will give information about command-line history of the sudo user
(10)
exit
history > commandlinehistory.txt
--> -it will give information about command-line history of regular user
(11)
tshark -J 'tcp http' > httptraffic.txt
--> capture HTTP traffic - after 1 minute CTRL+C to cancel (if it does not work try "sudo su" at first.)
(12)
tshark -J 'tcp https' > httptraffic.txt
--> capture HTTPS traffic - after 1 minute CTRL+C to cancel (if it does not work try "sudo su" at first.)
(13)
tshark -i eth0 -f "src port 53" -n -T fields -e dns.qry.name -e dns.a > DNSqueries.txt
--> capture DNS query traffic - after 1 minute CTRL+C to cancel (if it does not work try "sudo su" at first.) (eth0 network interface - if it does not work "netstat -i" to find out your network interface info)
(14)
tshark -i eth0 -f "src port 53" -n -T fields -e dns.qry.name -e dns.a > DNSqueries.txt
--> capture DNS query traffic - after 1 minute CTRL+C to cancel (if it does not work try "sudo su" at first.) (eth0 network interface - if it does not work "netstat -i" to find out your network interface info)
(15)
ls -lha bin > binfiles.txt
ls -lha usr > usrfiles.txt
ls -lha usr/bin > usr-binfiles.txt
ls -lha usr/share > usr-sharefiles.txt
ls -lha usr/local> usr-localfiles.txt
ls -lha opt> optfiles.txt
(Run these commands separately to check if there is a new executable file under these folders)
(16)
crontab -l > crontabs1.txt
(Check crontabs to see if there is a persistent mechanism) (if it does not work try "sudo su" at first.)
(17)
cat /etc/crontab > crontabs2.txt
(Check crontabs to see if there is a persistent mechanism) (if it does not work try "sudo su" at first.)
(17)
find -type f -exec md5sum "{}" + > ~/HASHES.txt
(Collect all hash values under a directory with sub-directories)
(19) Capture Memory Image
(20) Analyze Linux Memory via Volatility
(21) Search Strings
(22) Check Some Specific Logs
- Use the Last or Last -F on the terminal to see display the list of all the users logged in and out since the file /var/log/wtmp was created. One or more usernames can be given as an argument to display their login in (and out) time and their host-name.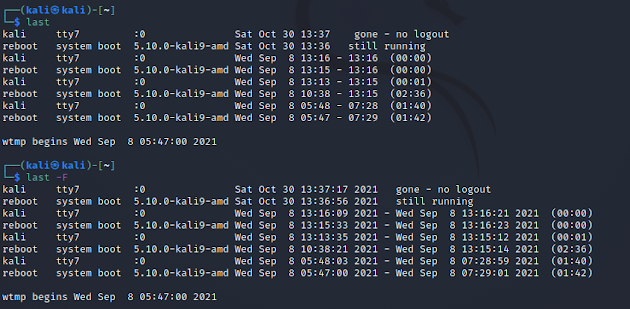
- Look at auth.log to check failure authentications or suspicious activities (you can focus on detection time)
- LINUX DFIR RECOMMENDATIONS:-- Check user /etc/passwd and group accounts /etc/group-- Check shells and history logs-- Search added/modified files-- Check running processes, locations, and configs-- Export and analyze timelines comparing normal and abnormal activities

by dfirist@gmail.com
by dfirist@gmail.com









Comments
Post a Comment